April 24, 2016 / Dennis Holinka
Topic 7 – Evaluating Emerging Technologies, Innovations & Trends
This week's posts go over the Evaluating Emerging Technologies, Innovations & Trends, the various perspectives, and related reflections in the blog.
Post 3 – Innovating Enterprise Value Chains
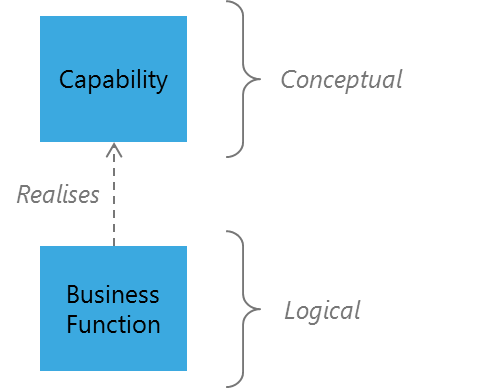
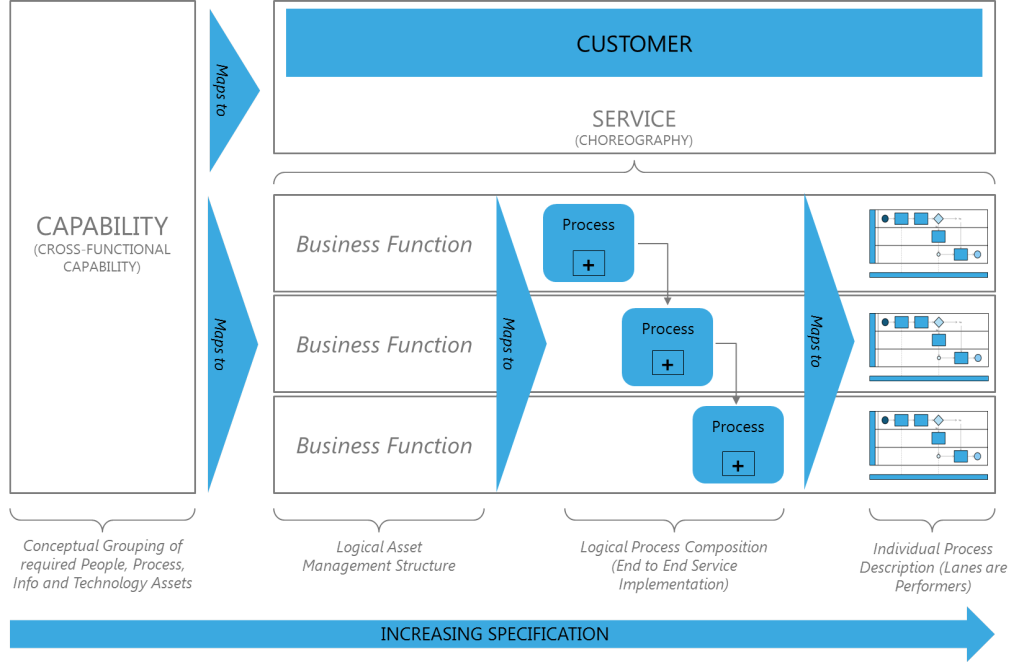
The evaluation of emerging trends, technologies, and innovations have provided multiple insights into the respective ideas that will lead to creative disruption in the conventional enterprise value chains. The three areas that have the greatest impact on the value chains today are related to Business Model Innovation, Service Digitalization, and Dynamic Business Process Management. These trends in innovation have created new expectations in the way business structure themselves and in the activities they seek to provide in order to provide value. The traditional value chains of Product, Marketing, Sales, Service, and Operations are giving way to organizational innovations and management innovations in order to provide for those trends. The conventional business model can be easily represented using a GODS architecture model that shows value chain and value add flow of the enterprise. That value chain can be furthered decomposed into value streams across the enterprise. IBM research indicated that there are at least 18 distinct value streams in an enterprise depending on factoring which can then be broken down into value stages according to the Business Architecture Guild. The Business Architecture Guild has demonstrated that there is a link between value stream stages and business processes and then links from business processes to IT services. The point of the matter is that the new trends operate by the decomposition, restructuring, and reconfiguration of business processes, value stages, value streams, and the enterprise value chain.
Figure: Restructure Value Chain
The business model innovation is enabled by new technologies but even more so by the fact that business models are being innovated in ways that were previously impossible due to the lack of technologies. For instance, the enablement of customer centricity, digital analytics, cloud, mobile, and social have provided an extended nexus of forces that allow business who were strictly consigned to their business models to dynamically reshape their business boundaries in order to quickly assimilate backward and forward supply chain integrations. According to Gartner, "IT has been an accelerating force in creating new ways of doing and optimizing business activities. Social and mobile technologies are the latest forces to proliferate business model innovations. Business models that previously applied in niche areas can now be applied to many different product and service types as new technologies completely change the economics."
Figure: Governance Operational Development Support Architecture Value Chain
The enterprise can be innovated using the business model canvas and the opportunity analysis canvas. Previous business model innovations were not possible given the limited technologies to implement them. However, the nexus of forces of mobile, social, digital analytics, and cloud have combined to provide an technology innovation underpinning to allow for the reassembling of business and opportunity models. The ability to provide such reshaping is from those technologies which allow you to deconstruct, restructure, and reconfigure those businesses into new forms. The new form now include the ability to provide Service Digitalization, a new innovation and trend to provide expanded product support beyond the base products and to connect related or orthogonal business services into the existing business offerings. Those connections would not be complete if it were not for the ability to build upon other innovations such as customer centricity and predictive analytics to seamlessly weave value into a rich user experience. According to Gartner, "The trend to provide computerized or 'digital' extensions to services has also become so important that, even in traditional manufacturing industries, the service element can sometimes become the more lucrative part of the total package to customers. By using the Internet as a delivery platform to provide remote tailored design, installation support, training, configuration advice, insurance, monitoring and analysis, peer customer networking or other service features, companies can add value or differentiate their offering."
Figure: Supply Chain Ecosystem Organigraph
(from slide 5: http://www.slideshare.net/fullscreen/anandsubramaniam/supply-chain-risk-management/5)
The richness of the new user experience comes from the agility and flexibility that can be customized into the user interactions. This possibility comes from the new innovation of dynamic business process management. No longer are business process of all sizes - long and short running - too rigid to be redirected but rather, the process technology can now mimic human interception by building it as part of the technology itself. The new changes in business process, business model, and service expansion would not be possible if there weren't addendum innovations in the People category besides Process and Technology. It is here that organizational innovations that allow for dynamic workflows between employees and knowledge sharing as well as management innovations in reward systems that allow for autonomous interactions which make that happen. According to Gartner, "... IT architectural components (service-oriented architecture [SOA], messaging, metadata process description, Internet connectivity, rule engines and simulation) have evolved to the point where processes can be continually, rather than periodically, reconfigured. In some cases, a process flow can even be modified midway through its execution. Valuable customer proposition breakthroughs are made possible via more-dynamic process flows, such as Delivery Intercept by UPS in the logistics industry. However, relatively few business leaders have yet grasped the enormous efficiency potential of this shift. It requires new ways of management thinking and organization design, as well as considerable technology investment."
Figure: Purpose Driven Enterprise