March
20, 2016 / Dennis Holinka
Topic 5 – Security Architecture Layer
This week's posts go over the Security Architecture Layer, the various perspectives, and related reflections in the blog.
Post 1 – Cloud Security for SaaS, PaaS, and IaaS
The advent of cloud computing has made securing the enterprise more difficult. As stated in the Gartner research reading, there is risk where "no assessor has gone". That means that all of the controls, processes, procedures, and governance mechanisms have been built over the decades for the internal captive data center. There has even been some security built for the business to business/customer (B2B/B2C) integration, but the use of hybrid and public cloud have called forth and into question all the historical know how of security controls as they apply to external entities. The use of public cloud SaaS, PaaS, and IaaS, have begun to create the demand for security architecture and solutions to provide confidentiality, integrity, availability, and safety (CIAS) in order to protect and assure the safety of the business outcomes enabled by information technology. Moreover, the advent of digital business technologies as a new business distribution channel has required that security be nimble yet highly disciplined so that it provides value add without setting up bureaucratic roadblocks to getting work done.
Recently, I worked on an effort to bring in the use of public PaaS/SaaS applications for Enterprise File Sharing Services and the use of Social Media for the Enterprise. Both of these solutions extend the storage and interaction of information outside the walls of the firm and bring with it risks that have not been assessed or mitigated ever before. The risks associated with the extended enterprise has never been dealt with in such a public manner nor has the business implications and technology issues been understood well enough to move at the speed of business IT. Even so, where there is a gap in protection, safety, or security, the market will emerge to provide add on solutions to make up for it.
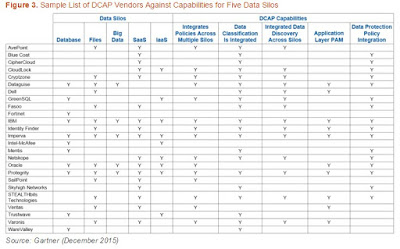
Gartner has characterized the advent of the type of solutions that are providing for what they are calling Data Centric Audit and Protection (DCAP). According to Gartner's Market Guide for DCAP, "DCAP is a category of products characterized by the ability to centrally manage data security policies and controls across unstructured, semistructured and structured repositories or silos. Based upon data security governance (DSG) principles, these products encompass the ability to classify and discover sensitive datasets and control access to the sensitive data by centrally managing and monitoring privileges and activity of users and administrators. Their ability to detect unusual behavior can result in real-time responses such as alerting or blocking." These capabilities are very important in public cloud PaaS and SaaS in that security can be circumvented by external enterprise users or external rouge users. For example, enterprises that use Yammer will be exposed to potential data loss if an employee can post sensitive corporate information on the social channel. What has made this even more difficult to secure and created the need for intervention security pre and post brokering is that Microsoft is not locking the entry into channels to exist for one corporate subnet to the public cloud provider. It has allowed for the most flexible access to their services with the expectation that third parties will emerge to protect the channel. DCAP capabilities have been outlined by Gartner and there are products that are using different aspects of DCAP capabiliites to form four types of product offerings. The four product segments are database audit and protection (DAP), file-centric audit and protection (FCAP), cloud access security broker (CASB) and data protection (DP) using abilities such as tokenization, data masking, and encryption. Since there is no single solution that can meet all of the requirements of DCAP, the vendors in each of these spaces are merging into each other's capabilities across the data silos. The DCAP capabilities have been documented by Gartner.

Figure: DCAP - Gartner Research
http://www.gartner.com/document/3178623?ref=solrAll&refval=164946567&qid=858c3ad7f63df37892defe77cf75ea41
The abilities of each type of solution is dependent on how vendors are growing their capabilities in these respective spaces. Forrester has classified these solutions as permutations of Cloud Access Security Intelligence (CASI) Solutions . CASIs have formed to "discover cloud applications, monitor employee behavior, and prevent data leaks". In essence, the DCAP capabilities have been uniquely combined to provide specific use case security capabilities to assure business outcomes from the security architecture. The basic architecture of the extended proxy and non broker solutions is that a combination of broker based and api based pre/post event APIs provide the security protection to assure that enterprises protect the CIAS Secuiity requirements.
This has made the ability to protect business outcomes in the digital / cloud space difficult in comparison to the closed loop enterprise where controls and capabilities were administered internally using enterprise available software. The future of security architecture in the digital and cloud environments will present unique challenges and opportunities to revisit all of the controls and assumptions that enterprise controls are based as developers, architects, and IT professionals try to bring discipline and security to the extended enterprise that requires flexibility to expand its supply chain processes outside of the immediate enterprise.
Figure: CASI - Forrester Research
This has made the ability to protect business outcomes in the digital / cloud space difficult in comparison to the closed loop enterprise where controls and capabilities were administered internally using enterprise available software. The future of security architecture in the digital and cloud environments will present unique challenges and opportunities to revisit all of the controls and assumptions that enterprise controls are based as developers, architects, and IT professionals try to bring discipline and security to the extended enterprise that requires flexibility to expand its supply chain processes outside of the immediate enterprise.
Figure: Market Guide for DCAP - Gartner Research
Figure: Market Guide for CASB - Gartner Research


Such a clear view on how Salesforce is related to Cloud Computing, hope your blog will reach more visitors who are all searching for the Cloud and Salesforce related updates.
ReplyDeleteRegards:
salesforce administrator training in chennai
Salesforce certification Training in Chennai
Excellent Blog!! What you explained is absolutely correct, at present CRM helps to track your customer effectively. Your ideas to extend the functionality in CRM will definitely help more to use CRM effectively. I found the best ways to get leads to my business.
ReplyDeleteMicrosoft Windows Azure Training | Online Course | Certification in chennai | Microsoft Windows Azure Training | Online Course | Certification in bangalore | Microsoft Windows Azure Training | Online Course | Certification in hyderabad | Microsoft Windows Azure Training | Online Course | Certification in pune